Generate Client Certificate From Private Key
The Certificate Authority (CA) provides you with your SSL Certificate (public key file). You use your server to generate the associated private key file where the CSR was created. You need both the public key and private keys for an SSL certificate to work properly on any system. Apr 12, 2020 Create server and client certificates using openssl for end to end encryption with Apache over SSL; Create SAN Certificate to protect multiple DNS, CN and IP Addresses of the server in a single certificate. These are the brief list of steps to create Certificate Authority using OpenSSL: Create private key to be used for the certificate. The client certificate was given to me by the third party, but it does not contain any private key. Giving you your certificate without its private key seems a bit pointless, unless you're expected to have generated a certificate request on your side beforehand (in which case you would have the private key).
- Certificate With Private Key
- Add Private Key To Certificate
- Generate Client Certificate From Private Key To Computer
Get started with Key Vault certificates.; 4 minutes to read +7; In this article. The following scenarios outline several of the primary usages of Key Vault’s certificate management service including the additional steps required for creating your first certificate in your key vault. Look for a folder called REQUEST or 'Certificate Enrollment Request Certificates. Select the private key that you wish to backup. Right click on the file and choose All Tasks Export. The certificate export wizard will start, please click Next to continue. In the next window select Yes, export the private key and click Next. Mar 29, 2016 In the same way we extracted the server’s public key, we can extract the client’s public key with the following command. This generates a file called client.cert containing the public certificate from the client.jks keystore. Apr 09, 2020 Generate a server private key using a utility (OpenSSL, cfssl etc) Create a CSR using the server private key. Generate the server certificate using CA key, CA cert and Server CSR. Also Read: Types of SSL/TLS Certificates Explained.
-->Point-to-Site connections use certificates to authenticate. This article shows you how to create a self-signed root certificate and generate client certificates using PowerShell on Windows 10 or Windows Server 2016. If you are looking for different certificate instructions, see Certificates - Linux or Certificates - MakeCert.
You must perform the steps in this article on a computer running Windows 10 or Windows Server 2016. The PowerShell cmdlets that you use to generate certificates are part of the operating system and do not work on other versions of Windows. The Windows 10 or Windows Server 2016 computer is only needed to generate the certificates. Once the certificates are generated, you can upload them, or install them on any supported client operating system.
If you do not have access to a Windows 10 or Windows Server 2016 computer, you can use MakeCert to generate certificates. The certificates that you generate using either method can be installed on any supported client operating system.
Create a self-signed root certificate
Use the New-SelfSignedCertificate cmdlet to create a self-signed root certificate. For additional parameter information, see New-SelfSignedCertificate.
From a computer running Windows 10 or Windows Server 2016, open a Windows PowerShell console with elevated privileges. These examples do not work in the Azure Cloud Shell 'Try It'. You must run these examples locally.
Use the following example to create the self-signed root certificate. The following example creates a self-signed root certificate named 'P2SRootCert' that is automatically installed in 'Certificates-Current UserPersonalCertificates'. You can view the certificate by opening certmgr.msc, or Manage User Certificates.
Leave the PowerShell console open if you want to create a client certificate right after creating this root certificate.
Generate a client certificate
Each client computer that connects to a VNet using Point-to-Site must have a client certificate installed. You generate a client certificate from the self-signed root certificate, and then export and install the client certificate. If the client certificate is not installed, authentication fails.
The following steps walk you through generating a client certificate from a self-signed root certificate. You may generate multiple client certificates from the same root certificate. When you generate client certificates using the steps below, the client certificate is automatically installed on the computer that you used to generate the certificate. If you want to install a client certificate on another client computer, you can export the certificate.
The examples use the New-SelfSignedCertificate cmdlet to generate a client certificate that expires in one year. For additional parameter information, such as setting a different expiration value for the client certificate, see New-SelfSignedCertificate.
Example 1 - PowerShell console session still open
Use this example if you have not closed your PowerShell console after creating the self-signed root certificate. This example continues from the previous section and uses the declared '$cert' variable. If you closed the PowerShell console after creating the self-signed root certificate, or are creating additional client certificates in a new PowerShell console session, use the steps in Example 2.
Modify and run the example to generate a client certificate. If you run the following example without modifying it, the result is a client certificate named 'P2SChildCert'. If you want to name the child certificate something else, modify the CN value. Do not change the TextExtension when running this example. The client certificate that you generate is automatically installed in 'Certificates - Current UserPersonalCertificates' on your computer.
Example 2 - New PowerShell console session
If you are creating additional client certificates, or are not using the same PowerShell session that you used to create your self-signed root certificate, use the following steps:
Identify the self-signed root certificate that is installed on the computer. This cmdlet returns a list of certificates that are installed on your computer.
Locate the subject name from the returned list, then copy the thumbprint that is located next to it to a text file. In the following example, there are two certificates. The CN name is the name of the self-signed root certificate from which you want to generate a child certificate. In this case, 'P2SRootCert'.
Declare a variable for the root certificate using the thumbprint from the previous step. Replace THUMBPRINT with the thumbprint of the root certificate from which you want to generate a child certificate.
For example, using the thumbprint for P2SRootCert in the previous step, the variable looks like this:
Modify and run the example to generate a client certificate. If you run the following example without modifying it, the result is a client certificate named 'P2SChildCert'. If you want to name the child certificate something else, modify the CN value. Do not change the TextExtension when running this example. The client certificate that you generate is automatically installed in 'Certificates - Current UserPersonalCertificates' on your computer.
Export the root certificate public key (.cer)
After creating a self-signed root certificate, export the root certificate public key .cer file (not the private key). You will later upload this file to Azure. The following steps help you export the .cer file for your self-signed root certificate:
To obtain a .cer file from the certificate, open Manage user certificates. Locate the self-signed root certificate, typically in 'Certificates - Current UserPersonalCertificates', and right-click. Click All Tasks, and then click Export. This opens the Certificate Export Wizard. If you can't find the certificate under Current UserPersonalCertificates, you may have accidentally opened 'Certificates - Local Computer', rather than 'Certificates - Current User'). If you want to open Certificate Manager in current user scope using PowerShell, you type certmgr in the console window.
In the Wizard, click Next.
Select No, do not export the private key, and then click Next.
On the Export File Format page, select Base-64 encoded X.509 (.CER)., and then click Next.
For File to Export, Browse to the location to which you want to export the certificate. For File name, name the certificate file. /generate-an-ssh-key-for-gitlab.html. Then, click Next.
Click Finish to export the certificate.
Your certificate is successfully exported.
The exported certificate looks similar to this:
If you open the exported certificate using Notepad, you see something similar to this example. The section in blue contains the information that is uploaded to Azure. If you open your certificate with Notepad and it does not look similar to this, typically this means you did not export it using the Base-64 encoded X.509(.CER) format. Additionally, if you want to use a different text editor, understand that some editors can introduce unintended formatting in the background. This can create problems when uploaded the text from this certificate to Azure.
Export the self-signed root certificate and private key to store it (optional)
You may want to export the self-signed root certificate and store it safely as backup. If need be, you can later install it on another computer and generate more client certificates. To export the self-signed root certificate as a .pfx, select the root certificate and use the same steps as described in Export a client certificate.
Export the client certificate
When you generate a client certificate, it's automatically installed on the computer that you used to generate it. If you want to install the client certificate on another client computer, you need to export the client certificate that you generated.
To export a client certificate, open Manage user certificates. The client certificates that you generated are, by default, located in 'Certificates - Current UserPersonalCertificates'. Right-click the client certificate that you want to export, click all tasks, and then click Export to open the Certificate Export Wizard.
In the Certificate Export Wizard, click Next to continue.
Select Yes, export the private key, and then click Next.
On the Export File Format page, leave the defaults selected. Make sure that Include all certificates in the certification path if possible is selected. This setting additionally exports the root certificate information that is required for successful client authentication. Without it, client authentication fails because the client doesn't have the trusted root certificate. Then, click Next.
On the Security page, you must protect the private key. If you select to use a password, make sure to record or remember the password that you set for this certificate. Then, click Next.
On the File to Export, Browse to the location to which you want to export the certificate. For File name, name the certificate file. Then, click Next.
Click Finish to export the certificate.
Install an exported client certificate
Each client that connects to the VNet over a P2S connection requires a client certificate to be installed locally.
To install a client certificate, see Install a client certificate for Point-to-Site connections.
Next steps
Continue with your Point-to-Site configuration.
- For Resource Manager deployment model steps, see Configure P2S using native Azure certificate authentication.
- For classic deployment model steps, see Configure a Point-to-Site VPN connection to a VNet (classic).
Certificate With Private Key
The following scenarios outline several of the primary usages of Key Vault’s certificate management service including the additional steps required for creating your first certificate in your key vault.
The following are outlined:
- Creating your first Key Vault certificate
- Creating a certificate with a Certificate Authority that is partnered with Key Vault
- Creating a certificate with a Certificate Authority that is not partnered with Key Vault
- Import a certificate
Certificates are complex objects
Certificates are composed of three interrelated resources linked together as a Key Vault certificate; certificate metadata, a key, and a secret.
Creating your first Key Vault certificate
Before a certificate can be created in a Key Vault (KV), prerequisite steps 1 and 2 must be successfully accomplished and a key vault must exist for this user / organization.
Step 1 - Certificate Authority (CA) Providers
- On-boarding as the IT Admin, PKI Admin or anyone managing accounts with CAs, for a given company (ex. Contoso) is a prerequisite to using Key Vault certificates.
The following CAs are the current partnered providers with Key Vault:- DigiCert - Key Vault offers OV TLS/SSL certificates with DigiCert.
- GlobalSign - Key Vault offers OV TLS/SSL certificates with GlobalSign.
Step 2 - An account admin for a CA provider creates credentials to be used by Key Vault to enroll, renew, and use TLS/SSL certificates via Key Vault.
Step 3 - A Contoso admin, along with a Contoso employee (Key Vault user) who owns certificates, depending on the CA, can get a certificate from the admin or directly from the account with the CA.
- Begin an add credential operation to a key vault by setting a certificate issuer resource. A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Ex. MyDigiCertIssuer
- Provider
- Credentials – CA account credentials. Each CA has its own specific data.
For more information on creating accounts with CA Providers, see the related post on the Key Vault blog.
Step 3.1 - Set up certificate contacts for notifications. This is the contact for the Key Vault user. Key Vault does not enforce this step.
Note - This process, through step 3.1, is a onetime operation.
Creating a certificate with a CA partnered with Key Vault
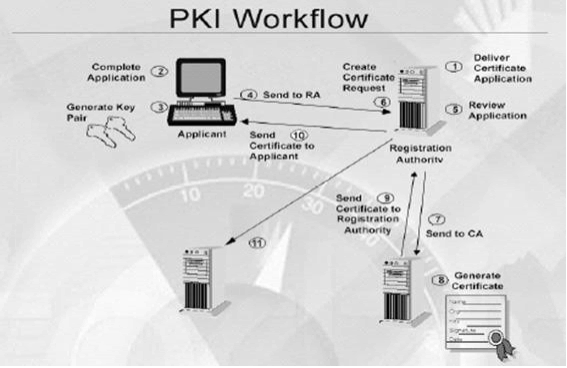
Step 4 - The following descriptions correspond to the green numbered steps in the preceding diagram.
(1) - In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
(2) - Key Vault sends an TLS/SSL Certificate Request to the CA.
(3) - Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
(4) - The CA responds to Key Vault's TLS/SSL Certificate Request with an X509 TLS/SSL Certificate.
(5) - Your new certificate creation completes with the merger of the X509 Certificate for the CA.
Key Vault user – creates a certificate by specifying a policy
Repeat as needed
Policy constraints
- X509 properties
- Key properties
- Provider reference - > ex. MyDigiCertIssure
- Renewal information - > ex. 90 days before expiry
A certificate creation process is usually an asynchronous process and involves polling your key vault for the state of the create certificate operation.
Get certificate operation- Status: completed, failed with error information or, canceled
- Because of the delay to create, a cancel operation can be initiated. The cancel may or may not be effective.
Import a certificate
Alternatively – a cert can be imported into Key Vault – PFX or PEM.
Import certificate – requires a PEM or PFX to be on disk and have a private key.
You must specify: vault name and certificate name (policy is optional)
PEM / PFX files contains attributes that KV can parse and use to populate the certificate policy. If a certificate policy is already specified, KV will try to match data from PFX / PEM file.
Once the import is final, subsequent operations will use the new policy (new versions).
If there are no further operations, the first thing the Key Vault does is send an expiration notice.
Also, the user can edit the policy, which is functional at the time of import but, contains defaults where no information was specified at import. Ex. no issuer info
Add Private Key To Certificate
Formats of Import we support
We support the following type of Import for PEM file format. A single PEM encoded certificate along with a PKCS#8 encoded, unencrypted key which has the following
-----BEGIN CERTIFICATE----------END CERTIFICATE-----
-----BEGIN PRIVATE KEY----------END PRIVATE KEY-----
On certificate merge we support 2 PEM based formats. You can either merge a single PKCS#8 encoded certificate or a base64 encoded P7B file.-----BEGIN CERTIFICATE----------END CERTIFICATE-----
We currently don't support EC keys in PEM format.
Creating a certificate with a CA not partnered with Key Vault
This method allows working with other CAs than Key Vault's partnered providers, meaning your organization can work with a CA of its choice.
The following step descriptions correspond to the green lettered steps in the preceding diagram.
(1) - In the diagram above, your application is creating a certificate, which internally begins by creating a key in your key vault.
(2) - Key Vault returns to your application a Certificate Signing Request (CSR).
(3) - Your application passes the CSR to your chosen CA.
(4) - Your chosen CA responds with an X509 Certificate.
Generate Client Certificate From Private Key To Computer
(5) - Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.