Python Generate Aes Key From Password
Need to encrypt some text with a password or private key in Python? You certainly came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself.
- Python Aes Decrypt
- Python Generate Aes Key From Password Windows 7
- Python Generate Aes Key From Password Windows 10
“Believe in your infinite potential. Your only limitations are those you set upon yourself.” ― Roy T. Bennett, The Light in the Heart
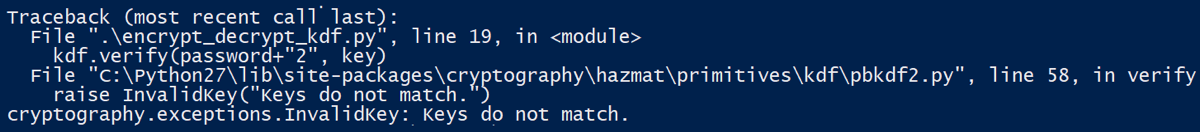
#!/usr/bin/env python from Crypto.Cipher import AES import base64 import os # the block size for the cipher object; must be 16 per FIPS-197 BLOCKSIZE = 16 # the character used for padding-with a block cipher such as AES, the value # you encrypt must be a multiple of BLOCKSIZE in length. Scrypt: Scrypt is used to generate a secure private key from the password. This will make it harder for an attacker to brute-force our encryption. Salt: A new random salt is used for each run of our encryption. This makes it impossible for an attacker to use precomputed hashes in an attempt to crack the cipher. Jun 25, 2010 We create a new AES encryptor object with Crypto.Cipher.AES.new, and give it the encryption key and the mode. Next comes the encryption itself. Next comes the encryption itself. Again, since the API is low-level, the encrypt method expects your input to consist of an integral number of 16-byte blocks (16 is the size of the basic AES block). Python 3 introduced key derivation functions, which are especially convenient when storing passwords. Both pbkdf2 and scrypt are provided. While scrypt is more robust against attacks as it is both memory- and CPU-heavy, it only works on systems that provide OpenSSL 1.1+. Let's illustrate the AES encryption and AES decryption concepts through working source code in Python. The first example below will illustrate a simple password-based AES encryption (PBKDF2 + AES-CTR) without message authentication (unauthenticated encryption).The next example will add message authentication (using the AES-GCM mode), then will add password to key derivation (AES-256-GCM. PBKDF2 (Password Based Key Derivation Function 2) is typically used for deriving a cryptographic key from a password. In this example, you’ll this function to generate a key from a password and use that key to create the Fernet object for encrypting and decrypting data. In this case, the data to encrypt is a simple message string.
Contents
- 6. File Encryption with AES
- Conclusion
1. Introduction
Pycrypto is a python module that provides cryptographic services. Pycrypto is somewhat similar to JCE (Java Cryptography Extension) for Java. In our experience JCE is more extensive and complete, and the documentation for JCE is also more complete. That being said, pycrypto is a pretty good module covering many aspects of cryptography.
In this article, we investigate using pycrypto’s implementation of AES for file encryption and decryption.
[Note: We have also covered AES file encryption and decryption in java previously.]
2. Generating a Key
AES encryption needs a strong key. The stronger the key, the stronger your encryption. This is probably the weakest link in the chain. By strong, we mean not easily guessed and has sufficient entropy (or secure randomness).
That being said, for the sake of demonstration of AES encryption, we generate a random key using a rather simple scheme. Do not copy and use this key generation scheme in production code.
AES encryption needs a 16-byte key.
3. Initialization Vector
In addition to the key, AES also needs an initialization vector. This initialization vector is generated with every encryption, and its purpose is to produce different encrypted data so that an attacker cannot use cryptanalysis to infer key data or message data.
A 16-byte initialization vector is required which is generated as follows.
The initialization vector must be transmitted to the receiver for proper decryption, but it need not be kept secret. It is packed into the output file at the beginning (after 8 bytes of the original file size), so the receiver can read it before decrypting the actual data.
4. Encrypting with AES
We now create the AES cipher and use it for encrypting a string (or a set of bytes; the data need not be text only).
The AES cipher is created with CBC Mode wherein each block is “chained” to the previous block in the stream. (You do not need to know the exact details unless you are interested. All you need to know is – use CBC mode).
Also, for AES encryption using pycrypto, you need to ensure that the data is a multiple of 16-bytes in length. Pad the buffer if it is not and include the size of the data at the beginning of the output, so the receiver can decrypt properly.
5. Decrypting with AES
Decryption requires the key that the data was encrypted with. You need to send the key to the receiver using a secure channel (not covered here).
In addition to the key, the receiver also needs the initialization vector. This can be communicated as plain text, no need for encryption here. One way to send this is to include it in the encrypted file, at the start, in plaintext form. We demonstrate this technique below (under File Encryption with AES). For now, we assume that the IV is available.
And that is how simple it is. Now read on to know how to encrypt files properly.
6. File Encryption with AES
We have three issues to consider when encrypting files using AES. We explain them in detail below.

First step is to create the encryption cipher.
6.1. Write the Size of the File
First we have to write the size of the file being encrypted to the output. This is required to remove any padding applied to the data while encrypting (check code below).
Determine the size of the file.
Open the output file and write the size of the file. We use the struct package for the purpose.
6.2. Save the Initialization Vector
As explained above, the receiver needs the initialization vector. Write the initialization vector to the output, again in clear text.
6.3. Adjust Last Block
The third issue is that AES encryption requires that each block being written be a multiple of 16 bytes in size. So we read, encrypt and write the data in chunks. The chunk size is required to be a multiple of 16.
This means the last block written might require some padding applied to it. This is the reason why the file size needs to be stored in the output.
Here is the complete write code.
7. Decrypting File Using AES
Now we need to reverse the above process to decrypt the file using AES.
First, open the encrypted file and read the file size and the initialization vector. The IV is required for creating the cipher.
Next create the cipher using the key and the IV. We assume the key has been communicated using some other secure channel.
We also write the decrypted data to a “verification file”, so we can check the results of the encryption and decryption by comparing with the original file.
Note that when the last block is read and decrypted, we need to remove the padding (if any has been applied). This is where we need the original file size.
Conclusion
And that is all there is to encrypting and decrypting a file using AES in python. We need to generate or obtain a key, create the initialization vector and write the original file size followed by the IV into the output file. This is followed by the encrypted data. Finally decryption does the same process in reverse.
Encrypt data with AES¶
The following code generates a new AES128 key and encrypts a piece of data into a file.We use the EAX mode because it allows the receiver to detect anyunauthorized modification (similarly, we could have used other authenticatedencryption modes like GCM, CCM or SIV).
At the other end, the receiver can securely load the piece of data back (if they know the key!).Note that the code generates a ValueError exception when tampering is detected.
Generate an RSA key¶
The following code generates a new RSA key pair (secret) and saves it into a file, protected by a password.We use the scrypt key derivation function to thwart dictionary attacks.At the end, the code prints our the RSA public key in ASCII/PEM format:
The following code reads the private RSA key back in, and then prints again the public key:
Generate public key and private key¶
The following code generates public key stored in receiver.pem and private key stored in private.pem. These files will be used in the examples below. Every time, it generates different public key and private key pair.
Python Aes Decrypt
Encrypt data with RSA¶
The following code encrypts a piece of data for a receiver we have the RSA public key of.The RSA public key is stored in a file called receiver.pem.
Since we want to be able to encrypt an arbitrary amount of data, we use a hybrid encryption scheme.We use RSA with PKCS#1 OAEP for asymmetric encryption of an AES session key.The session key can then be used to encrypt all the actual data.
Python Generate Aes Key From Password Windows 7
As in the first example, we use the EAX mode to allow detection of unauthorized modifications.
Python Generate Aes Key From Password Windows 10
The receiver has the private RSA key. They will use it to decrypt the session keyfirst, and with that the rest of the file: